PcapPoisoning
With the shark1.pcapng provided within the picoCTF site, the pcap is opened within wireshark. The packet list displays a large number of intercepted traffics, which can be seen below.
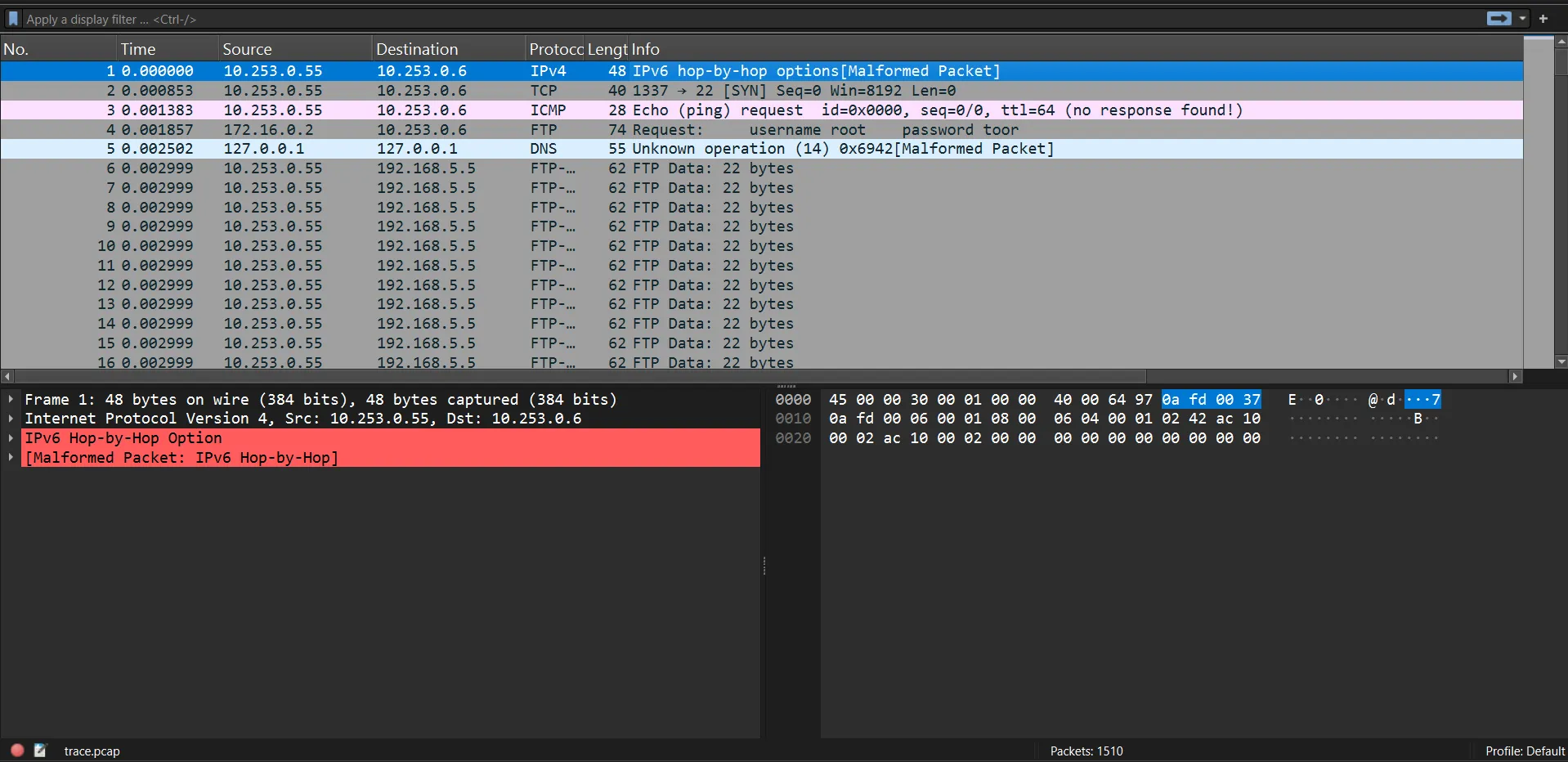 As seenable above, viewing the fourth packet, it particularly stands out with the username and password shared for an user.
As seenable above, viewing the fourth packet, it particularly stands out with the username and password shared for an user.
Filtering using the tcp.stream eq 1 within the display filter, the TCP steam following the fourth packet can be seen, which is packet 507. Viewing the decoded packet content in the packet bytes section, the flag can be seen.
ER@
P picoCTF{P64P_4N4L7S1S_SU55355FUL_f621fa37}
Related Writeups
Chunked Integrity
This is one of my favorite images! Unfortunately something has gone wrong and I cant see the whole thing, can you help f ...
Just Packets
Here pcap. Find flag.
Keeping on Schedule
One of our computers on the company network had some malware on it. We think we cleared of the main payload however it c ...
