KnightCal
by sealldev
🚩 CTFs KnightCTF 2025 web
KnightCal / KnightCTF 2025
Original Writeup on seall.dev
We are given a calculator webpage:
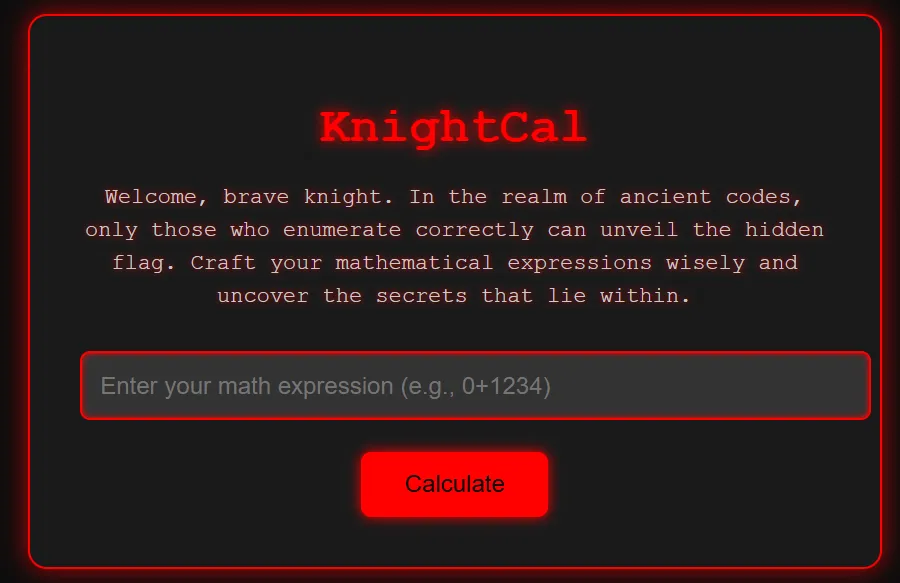
Trying the example payload 0+1234 we get:
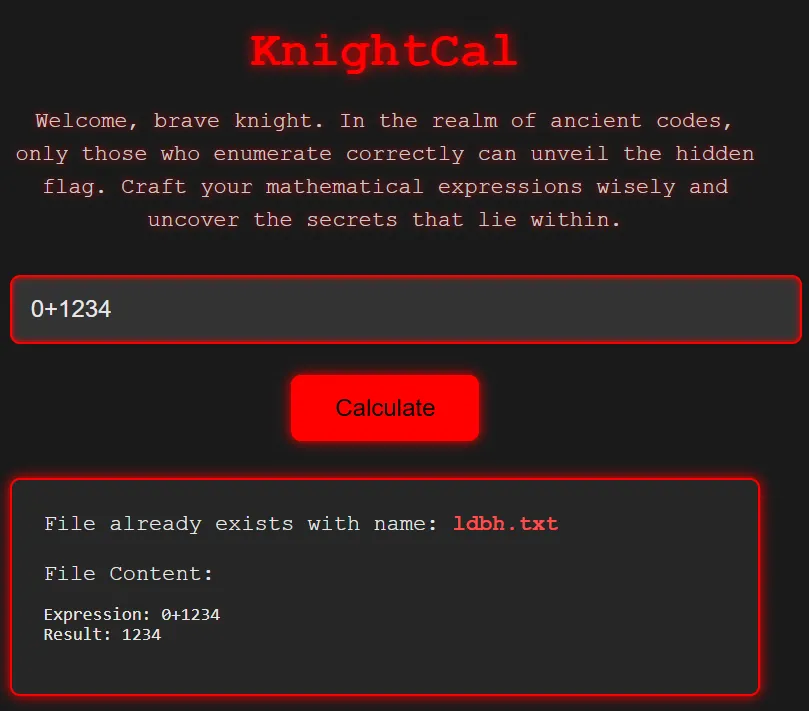
Trying all digits, we want to try to reconstruct the word flag to read flag.txt. Let’s try payload 0+123456789:
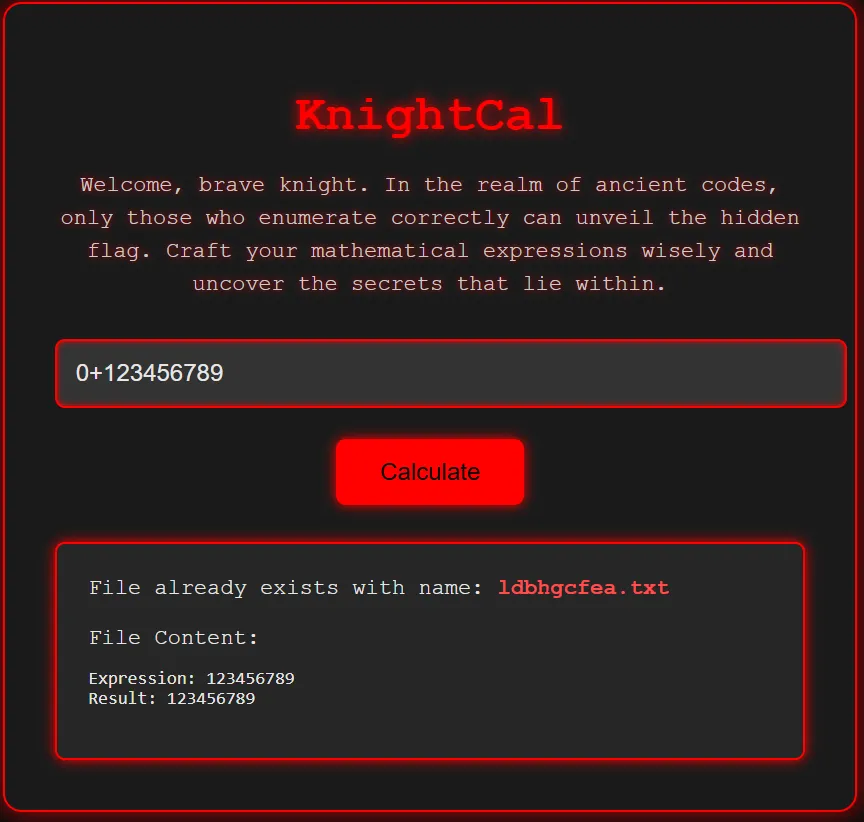
If 7=f, 1=l, 9=a and 5=g we can do 0+7195 to read the flag.
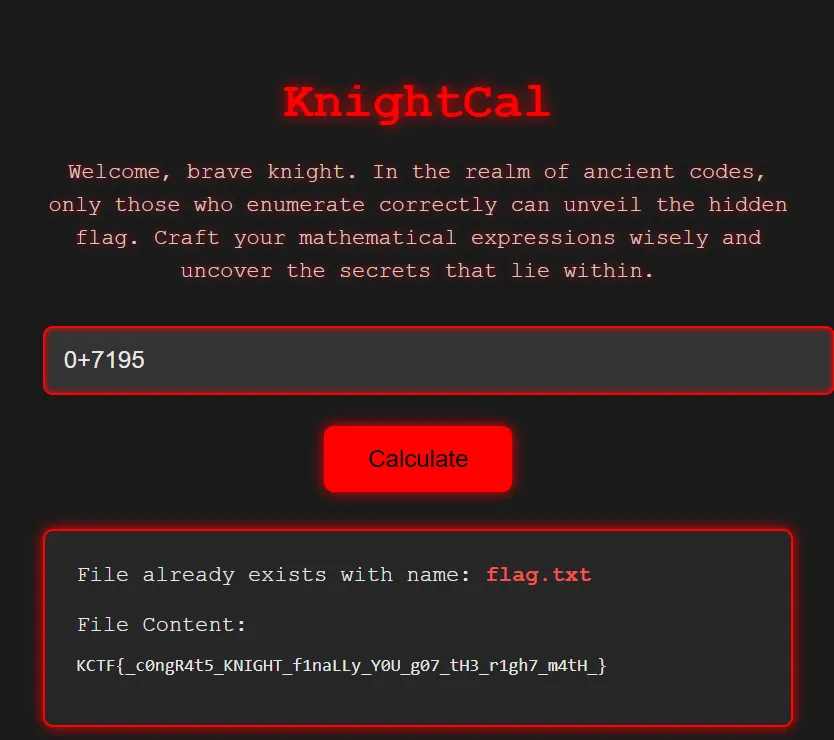
Flag: KCTF{_c0ngR4t5_KNIGHT_f1naLLy_Y0U_g07_tH3_r1gh7_m4tH_}
Related Writeups
l33t-benign
Now that you've figured out who was behind this operation, can you figure out who else was affected?
4spam
In the wake of last week's events, we've created a replacement (https://4spam.umbccd.net/). An old dump of some of the ...
Caddyshack
locate and connect to the server running on caddyshack.umbccd.net
