head-dump
by sealldev
easy
head-dump
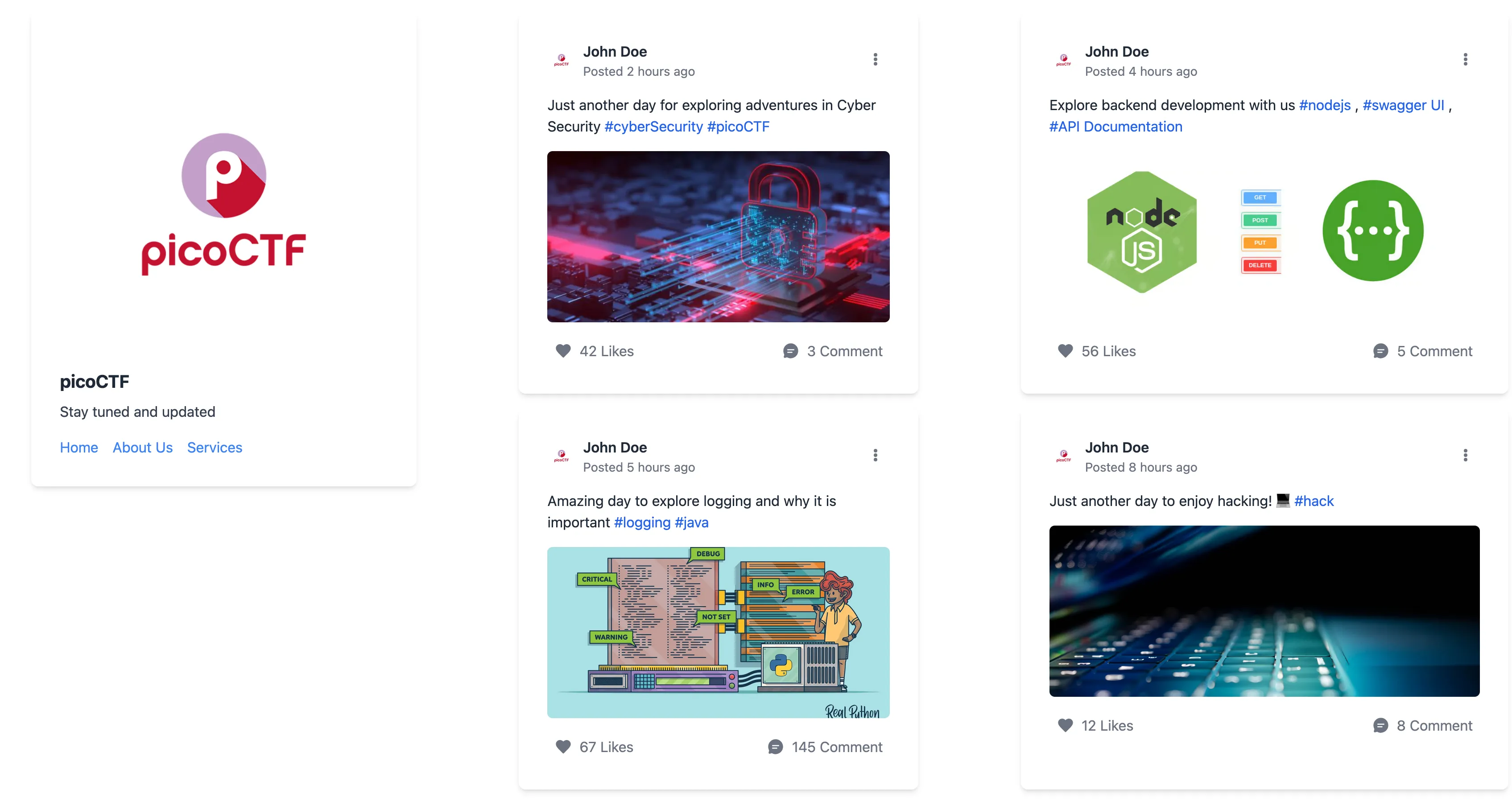
We start with a web instance showing some PicoCTF promo:
Reading through the source code, a specific segment catches my eye:
...
<!-- Message -->
<div class="mb-4">
<p class="text-gray-800">Explore backend development with us <a href="" class="text-blue-600">#nodejs</a> ,
<a href="" class="text-blue-600">#swagger UI</a> , <a href="/api-docs" class="text-blue-600 hover:underline">#API Documentation</a>
</p>
</div>
...
There is a hidden endpoint /api-docs!
Visiting it is a Swagger UI:
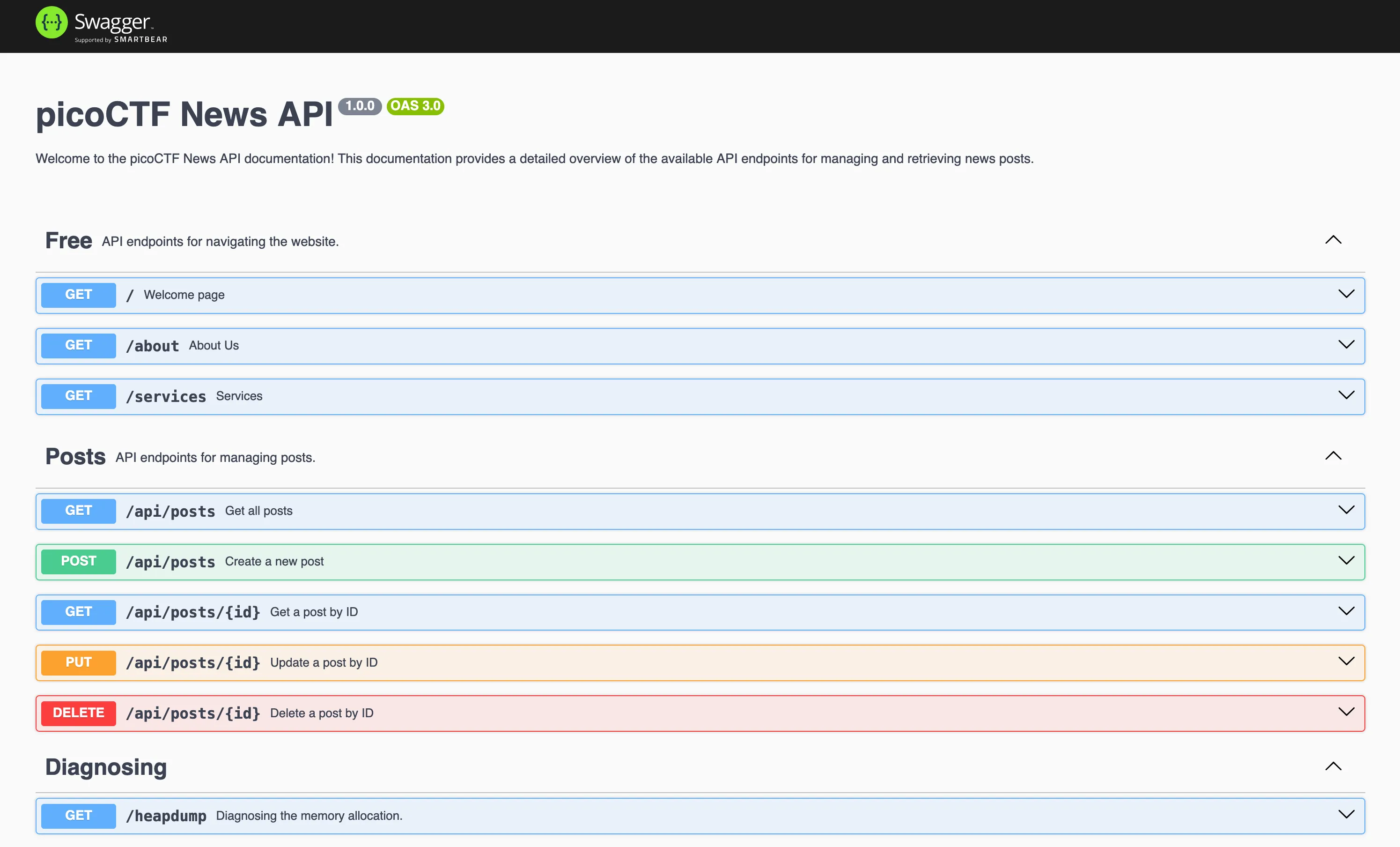
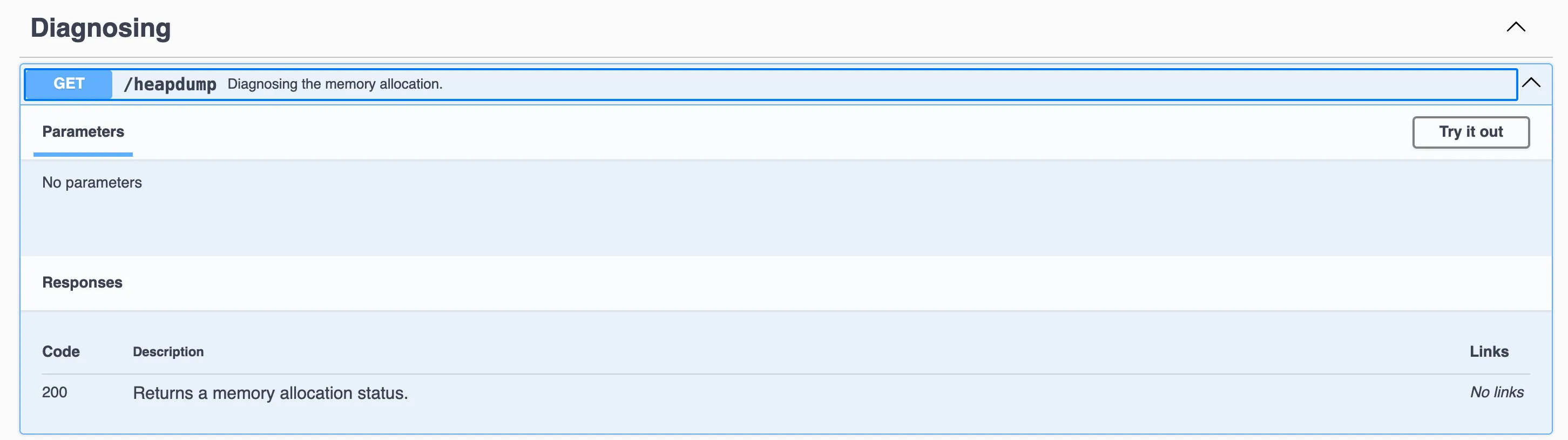
Inside the docs is a /heapdump endpoint!
I then used strings and grep to look for the flag:
$ strings ~/Downloads/heapdump-1742275987463.heapsnapshot | grep 'pico'
picoCTF{Pat!3nt_15_Th3_K3y_63fa652c}
...
Flag: picoCTF{Pat!3nt_15_Th3_K3y_63fa652c}
Related Writeups
l33t-benign
Now that you've figured out who was behind this operation, can you figure out who else was affected?
4spam
In the wake of last week's events, we've created a replacement (https://4spam.umbccd.net/). An old dump of some of the ...
Caddyshack
locate and connect to the server running on caddyshack.umbccd.net
